What is ZTNA?
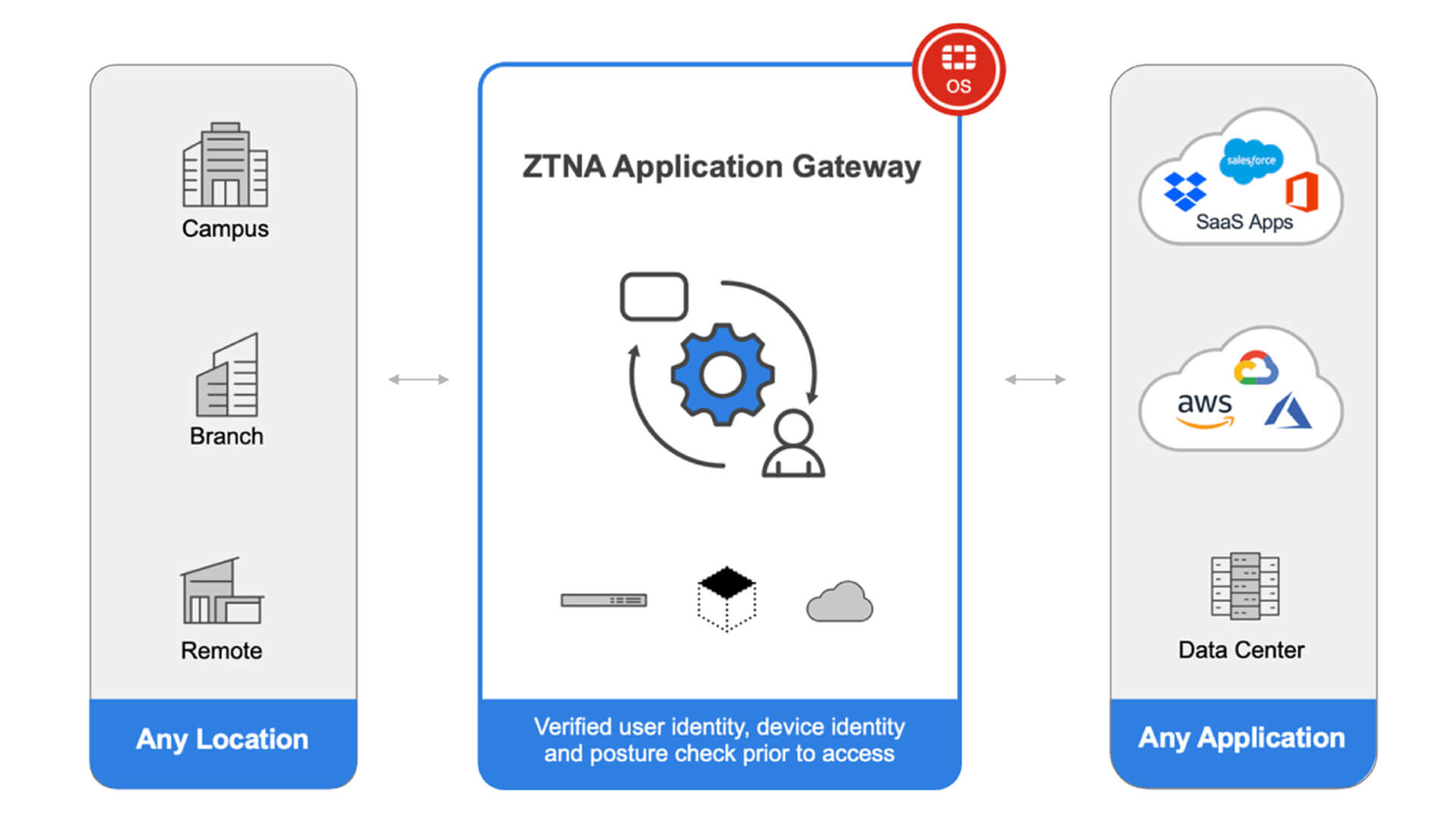
Fortinet ZTNA (Zero Trust Network Access) is a security solution that provides secure remote access to applications and resources within an enterprise, adhering to the zero-trust security model. Unlike traditional VPNs that grant broad access once a user connects, Fortinet ZTNA continuously evaluates and verifies the trustworthiness of users, devices, and applications throughout the session. In a zero-trust model, no user or device is automatically trusted, even if they are inside the network perimeter. Instead, every access request is subject to stringent identity verification and policy enforcement.
Fortinet ZTNA integrates with the Fortinet Security Fabric, including FortiGate firewalls, FortiAuthenticator, and FortiClient, to offer a comprehensive and unified approach to secure access management. This enables organizations to manage access control, monitor user behavior, and enforce policies consistently. The solution is particularly well-suited for environments with a high proportion of remote workers, cloud services, and mobile devices, ensuring secure access to resources from anywhere without the need for traditional VPN solutions.
With Fortinet ZTNA, organizations benefit from improved security, reduced attack surfaces, and simplified access management. It ensures that only authorized users and devices can access specific applications, thereby minimizing the risk of unauthorized access, data breaches, and insider threats.

Features & Benefits
Fortinet ZTNA enhances security by ensuring only authenticated users and devices can access critical applications, reducing the risk of unauthorized access and limiting potential attack vectors within the network.
It simplifies access control and improves user experience by providing seamless, secure access to applications, whether employees are on-site or remote, all while enforcing strict identity and device verification policies.
Ensures that all access requests are continuously authenticated and verified, minimizing the risk of unauthorized access to sensitive resources.
Supports the needs of remote workforces, cloud environments, and growing organizations by securely managing a large number of users and devices.
Provides precise control over who can access specific applications, enabling organizations to enforce policies based on user roles and device compliance.
Limits access to only necessary applications and resources, reducing exposure to potential threats and preventing lateral movement within the network.
Offers secure and transparent access to applications for users, whether they are working from the office or remotely, without compromising performance or security.
Leverages the broader Fortinet ecosystem for comprehensive, unified security, allowing for better threat detection, prevention, and response across the entire network.


 United Kingdom
United Kingdom Germany
Germany Denmark
Denmark Norway
Norway Sweden
Sweden Italy
Italy Finland
Finland































 Download Brochure
Download Brochure
 Schedule a Free Consultation
Schedule a Free Consultation