What is NAC?
Fortinet’s Network Access Control (NAC) solutions provide advanced tools to secure and manage access to enterprise networks. These solutions are designed to enforce strict access policies, ensuring that only authorized users and devices can connect to the network. By leveraging Fortinet’s NAC, organizations can enhance their cybersecurity posture while maintaining smooth network operations.
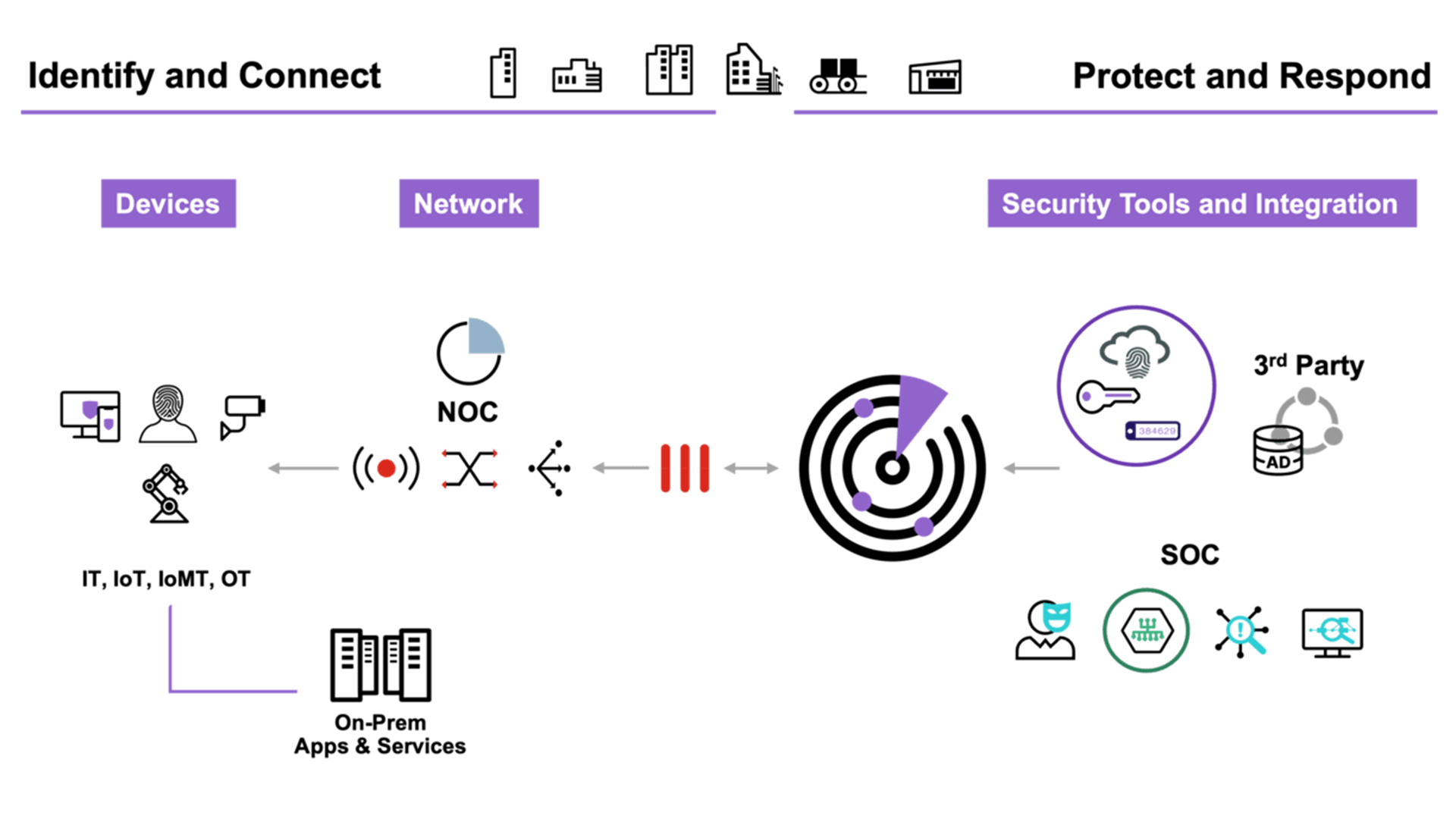
Fortinet NAC solutions integrate seamlessly with the Fortinet Security Fabric, offering centralized visibility and control over network access. They identify all devices attempting to connect to the network, verifying their compliance with security policies before granting access. This includes assessing device health, user identity, and other contextual factors. Unauthorized or non-compliant devices are automatically quarantined or denied access to mitigate potential security risks.
The solution supports a wide range of deployment scenarios, from small businesses to large enterprises, and can adapt to diverse network environments, including wired, wireless, and VPN connections. Its automation capabilities reduce administrative overhead by dynamically enforcing policies and responding to threats in real time.
Fortinet’s NAC provides several key benefits, such as improved network security, enhanced regulatory compliance, and streamlined access management. By controlling who and what connects to the network, organizations can minimize the risk of breaches, protect sensitive data, and ensure their networks operate efficiently and securely.


Features & Benefits
Fortinet’s Network Access Control (NAC) enhances network security by ensuring only authorized, compliant devices gain access. It improves visibility, allowing organizations to identify and control all connected devices.
With automated policy enforcement and threat response, it reduces administrative overhead. The solution supports regulatory compliance and adapts to diverse environments, helping businesses safeguard sensitive data, prevent breaches, and maintain efficient, secure network operations.
Ensures only authorized and compliant devices access the network.
Identifies and manages all devices attempting to connect.
Reduces administrative workload with dynamic enforcement and threat response.
Helps meet compliance standards by enforcing strict security policies.
Safeguards sensitive information and minimizes the risk of breaches.
Adapts to wired, wireless, and VPN network environments.


 United Kingdom
United Kingdom Germany
Germany Denmark
Denmark Norway
Norway Sweden
Sweden Italy
Italy Finland
Finland































 Download Brochure
Download Brochure
 Schedule a Free Consultation
Schedule a Free Consultation